The Ghost of Identity Past
Being a geek, I remember really well my first encounter with The Internet. Perhaps it’s because I am inevitably moving towards the older side of the IT professionals spectrum (not as far as punch cards though) and for today’s kids Internet is just the bread and butter of everyday life.
When I was 16, I visited the University of Economics in my hometown, where they had a network of workstations, the first place where The World Wide Web was accessible for anyone outside of the campus, including an ordinary kid like me. You had to log in to the shell to use the Internet. It didn’t take much for a a couple of talented students to emerge and replace the login binary asking for username and password with a script that was saving the credentials to a text file, politely alerting that you entered a wrong password and then calling the actual binary that should have been used in the first place. For as long as we had the concept of digital identity there have always been attempts to hack or bypass it.
Security was evolving, it was obvious, that networks running on IPv4 aren’t secure enough, after all, the protocol wasn’t developed with security in mind. We developed VPN’s, HTTPS running SSL, but they took a while to be widely implemented. I am old enough to remember using email servers which used plain HTTP (unencrypted web protocol) to log into the mailbox. My credentials travelled across the world wide web in plain text and anyone who was able to intercept (sniff) the traffic could then log into my account.
Every application needed some sort of accountability and audit, so the digital identity’s responsibility fell onto the application developers. We had more client applications running on the local computers than those which were accessible from a web browser, so inevitably we had millions of identity solutions which were proprietary and deeply embedded in the code of the application.
The concept of ‘everyone for themselves’ wasn’t providing great customer experience and we needed to remember a lot of passwords. On top of that we were realising that passwords in isolation are simply not secure enough.
In 2001 the OASIS Security Services Technical Committee (SSTC) met for the first time to discuss what would become the first iteration of SAML, released later on in 2002.
Slowly but surely we started to take leaps and the arrival of SSO (Single Sign On), MFA (Multi Factor Authentication), OAuth, SAML2 took us to the new era.
The Ghost of Identity Present
Fairly simple. If I was looking for the shortest summary of the identity today I would say:
Centralised identity service, decoupled from the application.
Long story short it means less work for developers, better customer experience, more security and dare I say an incredible source of information for business intelligence. Your login screen is no longer part of the application. In fact the login screen is shared across many applications and because identity became an application in itself, SSO (Single Sign On) is now easy to achieve and the best part is that it exists between organisations. Who doesn’t like logging in once a day and then consuming various applications without the need to re-enter credentials. It means I can log into my corporate intranet and then use an application provided to me by third party with a seamless experience. ‘The Login Service’ or what the identity folk call ‘The Identity Provider’ securely authenticates the user and passes some form of validation into the application (that’s where the assertions and tokens come into play). The application trusts the identity provider and establishes a session with the user without the need to maintain any log-in service itself.
It’s built on industry standards, out of which the most popular are SAML2 and OAuth2. It means that in principle if your application is federation aware (uses the above mentioned standards), you can change the identity provider fronting your application quite easily without any development work.
While the Ghost of Identity Present explains the above, there are still some naughty rascals who decide to build their own identity solutions. While it was normal in the eyes of the Ghost of Identity Past, today, they are what I refer to as identity freaks (the solutions, not those making them). They are proprietary (might as well say ‘dated’ right?), costly, difficult to manage and unlike the wine don’t get any better with time.
Enterprises are migrating to standards or their future could hang in the balance and become subjected to more and more risks.
Over the recent few years we took it to the next level and moved the identity service to cloud. From now on you can use it without the need to maintain the infrastructure yourself. IDaaS (Identity As A Service) is only changing the ‘where’ though, rather than the ‘how’.
The Ghost of Identity Future
It’s interesting, as we develop and put a lot of effort into centralised identity, we already know where the identity is going. It’s not about fraud prevention, machine learning algorithms to measure risk or password-less (that’s already the present), but about the most profound change that no-one expected. Decentralised identity. A true 180-degree turn.
Instead of the identity provider’s centralised store, a blockchain distributed ledger is now the source of truth for the successful verification (assertion) of the user. The ledger doesn’t contain any information about the user. It’s built on the same principle as the cryptocurrencies e.g. Bitcoin, Litecoin or Ethereal to name the few.
All the identity data is contained within the individual’s digital wallet, which makes its way there from ‘The Issuers’. User receives cryptographically signed ‘credentials’ from the government, employer, university, financial institution or a local authority like council etc. ‘The Verifiers’ are the services that are consuming the identity. That can be anything from banks (yes, an entity can be both issuer and consumer), on-line shops, streaming services… anything that requires identity.
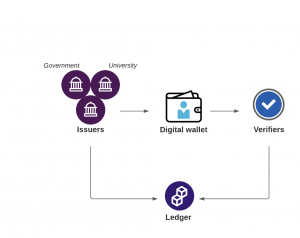
That way the user has the ability to fully control how the claims are used. For example you can sign up for a subscription which requires to prove you’re 18 or older but… you don’t have to share your date of birth. Another example would be obtaining license to watch on-line video content only for residents from a specific country, without sharing the exact address of residence.
It’s still being developed and it requires standardisation of protocols for a start. It’s likely that it will be developed in a way that provides an easy migration from ‘The Present’s’ centralised identity, so it should not stop you in your tracks if you are still living in the ‘Ghost of Identity Past’ tech state.
