
Most if not all heard about MFA (Multi-Factor Authentication), but on at least a few occasions I came across heated debates around the actual strength of the secondary factors.
Microsoft claims that MFA reduces account breaches by 99.9%, regardless of the second factor used (well almost). That’s a great number but for some that’s not quite enough. It’s fairly obvious that a credential attack at scale is nearing on impossible with the surface area of the attack so small (0.1%), but nevertheless, could a state sponsored group exploit the weaknesses of some secondary factors and if so, what are they?
Brute force
In my previous blog I was explaining different vectors of attacks against identity, but these were really related to classical username/password combinations. Does anyone take their chances brute-forcing MFA methods like OTP (One-Time Passcode). Well, actually they are. If you read Auth0’s The State Of Secure Identity report they say:
In the first four months of 2021, Auth0 logged more than 87,000 attempts to brute force
an OTP(…)
Now, I don’t know if that’s a lot or not, what’s the scale in comparison to all authentication events they had, but it’s obvious that the problem exists. I would be really interested in seeing how many of those were actually successful, but my suspicion is that a very small fraction if any at all. Until we have a full picture and more data we cannot rule this vector out completely. If there are bad guys trying, it must be worth their time, right?
Digital Identity Guidelines by NIST
NIST’s Special Publication 800-63B brings a new perspective to MFA dividing it into three assurance levels (AAL 1-3 – Authenticator Assurance Level). To make things more complicated, one of the parameters they us to measure the strength of the factor is if it’s a single-factor or a multi-factor… factor. It sounds complicated, but is really simple. If you remember the RSA SecurID tokens, which were displaying the 6 digit numbers valid for one minute (one time use), that was a single factor OTP (One Time Password). If you were required to put a pin into the dongle before receiving the code, that would be a multi-factor OTP. The single and multi factor parameter also applies to software authenticators. The debate starts when we talk about the authenticators on our mobile phones. Some of them (like Entrust) allows to ask for a PIN before displaying the code, making it a multi-factor software authenticator, some of them don’t – for example PingID mobile app can be opened without any additional protection (keep reading please), while their desktop equivalent is protected by a PIN. However, you cannot launch it without actually unlocking the phone. Many do not classify this as a multi-factor, but the fact remains that if your mobile is protected by PIN, you need to get through this hoop to reach the OTP.
Man-In-The-Middle
And there’s more than one type as far as MFA is concerned. First scenario is when you attack the transport layer in order to capture the MFA response. By transport layer we actually don’t mean OSI layer 3 and 4, in this case it’s the TLS (formerly known as SSL), which lives in layer 7 (application). In practice it means that the traffic from your device goes to the attacker, who then decrypts and re-encrypts the communication to the server. A good solution should be resistant to substituting the original certificate of the MFA server. And what’s a security measure can lead to our demise. If you do deep packet inspection on your firewalls (for legitimate reasons), your MFA might not work (at least the registration part). You may have to exclude this traffic from layer 7 inspection, just like you would the kind of traffic that is protected by regulators (for example in US you’re not supposed to deep inspect healthcare and banking communications).
Second use case is when you actually become a victim of phishing and it mimics the MFA interface. This kind of attack is only effective when you need to pass the OTP (one time passcode) back. NIST describes this as:
Authenticators that involve the manual entry of an authenticator output, such as out-of-band and OTP authenticators, SHALL NOT be considered verifier impersonation-resistant because the manual entry does not bind the authenticator output to the specific session being authenticated. In a MitM attack, an impostor verifier could replay the OTP authenticator output to the verifier and successfully authenticate
Push notifications
Just like pagers were pushed out by mobile phones, I think that at some point SMS, email and voice will be pushed out by authenticator applications. Not just because of customer experience and the need to actually do something (type the OTP in), but because of security. In general these are cryptographically strong and if they are the multi-factor type second factor, the level of difficulty to break increases by an order of magnitude. It’s no longer good enough to steal the credentials, but you have to also steal the mobile phone and be able to unlock it. As the technology evolves, authorities are able to bypass the security of some devices for the purpose of forensic investigations for instance, but the latest and greatest are usually unbreakable. Apple declined US government’s request to help with the investigation claiming, that even their technologists are not able to bypass the cryptographic security installed on their product (and the government actually then successfully broke it, but it wasn’t very cost effective, so we can park the idea at scale). While widely adopted by mobile providers, globally, push notifications are not available everywhere because of the local laws and regulations, so if you need to implement MFA in China for instance, you need to look at other methods. It is a minority though and who knows maybe in the future it will change.
Hard tokens
Pretty much considered the strongest of all and require physical connection to the device being unlocked. A good example will be Yubico’s Yubikeys. Or so we thought… In the eyes of NIST they are still single factor multi-factor devices. I only have to steal one in order to impersonate the user. They are fairly cheap and can easily replace mobile applications like authenticators, if that’s your appetite, but I would argue whether that’s stronger or not from a practical perspective, rather than the strength of cryptography. Most of us will know that we have lost our mobile phone almost immediately, but as far as the hard token is concerned we might find out on Monday morning, after the weekend, where everyone forgets about its existence.
Biometric hard tokens and WebAuthN
With the introduction of WebAuthN and FIDO2 we are entering the kind of ridiculous level of security that is pretty much unbreakable. At least it’s not very practical to attempt it, we are talking dark ops, spycraft techniques. With WebAuthN/FIDO2 passwords go away completely and you only use cryptography plus some form of hard token (it can be a single factor second factor, too, but let’s not focus on that here). Yubico have recently released a beautiful device, one they call a BIO Series. It’s a hard token, compatible with FIDO2 but you need a fingerprint to activate the authentication. This device can be lost and at least in principle becomes useless without the owner. With WebAuthN the concept of phishing goes away completely, but that’s a story for another day.
How does the market look like – what do others do?
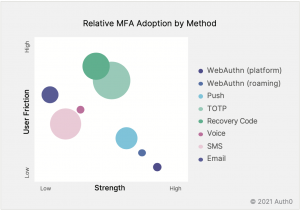
I will turn to Auth0’s The State Of Secure Identity once again. I highly recommend it for any identity professional. They were kind enough to show what MFA factors their customers prefer. The size of the circle represents relative adoption within their platform (see page 21 of the report for more narrative). They even go further breaking down to industry types in terms of method adoption. While ‘what everybody does’ is not an empiric gauge for security, it’s certainly something we should take into consideration while implementing MFA in our organisations.
Conclusion
Creating tables that rate the strength of different factors can be used as guides and most vendors will offer them to you, sometimes under NDA, but they will share the detail. I always think that customer experience is as important or right next to security, so hopefully in the future, when you brainstorm what’s best for your organisation as far as MFA is concerned, you can find the sweetspot, that gives you good enough security posture and excellent experience. Hopefully this blog has provided enough food for thought to make your own assessment and strength scale.