
Multi-factor authentication (MFA) – most of us have heard the term. Let’s take a closer look at what authentication is and why modern platforms utilise MFA.
What is the purpose of authentication?
It’s simple. Authentication confirms that you are, who you say you are. I am logging into my banking account and the bank requires username and password that is unique to me. In principle – by entering the right credentials I am proving it’s me. It’s not authentication’s role to figure out what I can do once inside the application. That’s authorisation’s task.
The problem arises if someone steals my credentials. The purpose of authentication is defeated, as the attacker gets access to the system and… well it’s not me.
What are the authentication factors?
In the realm of cyber security there are three.
Something you know
That’s the one we have been using for years. Username and password. It’s the cheapest to enforce and manage, but susceptible to theft and let’s be honest, we – as users don’t have a great track record of protecting passwords. And since they are in a digital (effectively virtual) form, there are no controls stopping us from copying the passwords from one place to another.
Something you have
This factor enhances the ‘something you know’ by removing the ability to copy the entity. Historically we used hardware tokens (the most known was SecurID RSA), but these days mobile phones or tablets took the majority of market’s use cases together with RFID key fobs or bracelets for proximity authentication and low cost, offline security keys (like Yubikey for example). If we wanted to be very precise, we would call it ‘something only you have’, as that is the purpose of this factor. The concept is much stronger that only knowing something, but still vulnerable. After all someone can steal my mobile phone and again if the attacker uses it to log into a system claiming it’s me, it defeats the purpose of the authentication process.
Something you are
The third and strongest of the three factors. It’s all about you, not something you know, have, but something you are. There are many ways to prove ‘you are really you’ and they revolve around biology and physics. While analysing DNA in real time is unlikely to be a cost effective solution anytime soon, there are other methods at hand. We use our fingerprint or facial recognition to unlock our phones. But it could also be voice or a retinal scan, but these methods are not so popular for variety of reasons.
This factor is the strongest of all three. In principle you cannot copy or steal it and also in principle you cannot spoof it. It obviously depends on the implementation, so every biometric system is evaluated and the two important parameters to consider are False Acceptance Rate (FAR) and False Rejection Rate (FRR). You probably heard about successful attempts to bypass iPhone’s FaceID with identical twins or TouchID with a replica of someone’s finger derived from a latent print lifted from a glass. Let’s not focus on that, as these are edge use cases and the fact remains that biometric security is the strongest.
Multi-Factor Authentication (MFA)
MFA means that the authentication process utilises more than one factor at the time of proving you are who you say you are. Theoretically it doesn’t matter which factor or whether we’ll use two or three factors, but the most common combination is factor 1&2 – username/password and a one time code delivered to our mobile phone. The code can be delivered in many forms, for example an SMS or an email.
Do I have to use MFA?
For many years we would just say ‘no’. Things have changed though. You may well have to use MFA in your systems as there are certain regulatory requirements depending on what your application is doing.
You may have come across another term SCA – Strong Customer Authentication. PSD2 (Payment Services Directive) is a set of laws and regulations for payment services in the EU and EEA. It is built on the same principle as MFA and without sounding ignorant… it’s about MFA and it governs that… you have to use it given specific criteria or data you are processing in the application.
Another reason for you to implement MFA is cyber insurance. The insurers demand more and more security controls in your solutions in order to renew and the first that comes up on the list is… MFA.
Why MFA?
There are many reasons and improving security or hardening the authentication process is only one of them. By simply adding additional factor you reduce the stolen credentials attack surface to near zero. You contribute to overall security posture of your user, both inside and outside of your application.
The benefits of using a well designed multi-factor authentication solution revolve around security, trust, compliance and last but not least customer experience. It’s also one that you get most of bang for the buck. With the era or public cloud, you no longer need to maintain the solution yourself. SaaS offerings add their value tremendously without much hated complexity and long time to execute.
Despite the stereotype that MFA hinders customer experience, new behavioural research shows that over 70% of consumers would choose passwordless MFA login over traditional usernames and passwords. Password + SMS is not quite passwordless yet, but it shows how our perception is evolving and how we become more security and privacy aware as digital society. Well balanced MFA gives security that the customers appreciate and great experience they desire.
But how do we take the MFA from good to great, what’s the cutting edge of identity experience these days?
Risk based authentication
Sometimes called the ‘context’, but it all sounds very enigmatic to an average Joe. It’s quite clever and simple though, but powered by sophisticated mechanisms of AI and machine learning (ML).
The best way to describe it is to map it to the existing framework and when you do, you arrive at conclusion that in fact it’s… somewhat of a fourth factor! No one dares to change the golden standard of the three authentication factors, so I’ll risk it, here’s the fourth authentication factor:
Something you do
We are all unique as human beings and we have our habits. Our habits are not as unique as genetics so they cannot really be part of ‘something you are’, after all there are many people watching 8pm news on TV. But if we combine few of them together they paint a picture of somewhat unique profile of ourselves. It may include geographical location, the type of operating system we use, browser and it’s version as well as when we do specific things (I start my work at 9am, so I am logging into my laptop somewhere around that time). The prime example of risk-based authentication is impossible travel protection. Imagine you logged in from your office in London. A malicious actor stole your credentials and is now trying to access your account from where they reside, let’s say 200 miles away. The time between your logins is 10 minutes. You cannot possibly make that journey within that timeframe. The risk is elevated and triggers compensating control. In our case a challenge for TOTP (time based one-time password) via an authenticator app (something you have). The attacker doesn’t have access to the TOTP and the threat doesn’t materialise. The sophisticated mechanisms of ML study your behaviour in order to catch anomaly and challenge it. Context can also put an end to the authentication journey if the risk is too high, despite using correct credentials.
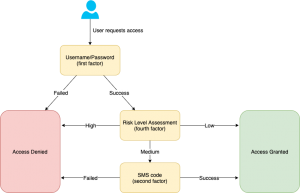
MFA in practice
Example of a simple but modern authentication flow
Fun facts about MFA
One of the earliest implementations of MFA was a code card, which for example bank would give to their customers in the early days of online banking. The authentication chain on the banking website would then request a specific code from the card (column, row) and authenticate the user that way. Funnily enough this concept is used to this day for… US nuclear launch procedure. They are called the ‘Gold Codes’ and issued on a card to the President and Vice-President of the United States. There’s also a ‘two-man rule’ in place which requires Secretary of State to co-authenticate the launch order of the president (or vice-president) through… you guessed it right – same MFA procedure and a code card.